
Psst… We received a tip…

The Breach That Stole Your Memory
It is 2030, and a hacker crew pulls off the kind of breach that becomes a reference point.
They hit one of the big cloud providers that hosts everyone’s “helpful” AI, then walk out with something far more valuable than credit card numbers, the context.
Millions of chat histories, long-running threads, saved memories, the little private explanations people only type when they think no one is listening.
Enterprise gets shredded, of course. And so do ordinary people.
Those stolen conversations are embarrassing, yes but they are also composable. You can mine them for routines, relationships, anxieties, writing style, and the exact phrases someone uses when they are tired and impressionable. If you want to impersonate a person convincingly, this is the dataset you would order.
This security problem hides inside the “personal AI” promise. The more your assistant knows you, the more a breach shifts from “data leaked” to a workable replica of you.
With the memory layer and enough context, an attacker can craft messages that land, slip through account recovery checks, and trigger real actions because they know your relationships, routines, and approval patterns.
So in response, the industry flips the default. Put more of the assistant on the local device, where the memory lives behind your lock screen instead of inside a shared data centre. Your phone handles the everyday work, learns your patterns locally, and only calls the cloud when it truly needs extra muscle. That does not make you invincible to security threats, but it changes the math.
This week we’re doing something a bit different and unpacking four patents that map the shift to on-device intelligence.
Here’s the inside scoop


Our paper boy trying to breach YOUR llm
The first patent shows how your device can handle most of the thinking and only ask for help when needed.
The second shows how a device can ask for help externally without oversharing.
The third shows how your model can learn on your hardware so it stays personal without exporting your life.
And the fourth shows how developers can package and update these models so everything stays fresh and stable.
Patent 1 - Artificial Intelligence on an Edge Network
Filed by Akamai Technologies.
Akamai runs a huge network of servers around the world that sit close to users. Websites and apps use that network to load faster and to filter out attacks, similar to what Cloudflare does and what the big clouds do with services like AWS CloudFront.
Akamai is patenting a tiered inference system that treats your device hardware as the first line of defense. The core mechanism is a confidence score. When you give a language model a task, a small model on your device attempts to solve it and generates a number representing how likely the answer is to be correct. If that score meets a specific threshold, the device provides that answer locally. If the score is too low, the request escalates to a more powerful model externally at the network edge or in the cloud.
For example, if you ask your phone to draft a text message, the local model can handle the task using your recent chat history for context. This happens instantly because it is an easy task so no data leaves the device. For a more complex task, such as summarizing a long legal document, the confidence score would drop. In that scenario, the phone sends only the necessary data to a stronger server to ensure accuracy. The system defaults to speed and privacy while keeping the cloud as a secondary backup.
Patent 2 - Edge device for collaborative inference based on semantic communications and method thereof
Filed by POSTECH Research and Business Development Foundation.
The researchers at POSTECH are focused on reducing the bandwidth required for AI to function. Their patent introduces a weak classifier that scans files to identify which parts carry the most information. Instead of uploading an entire high-resolution image, the device identifies target patches that contain relevant data and discards redundant patches like background noise or blank space. It transmits only the semantic information of those specific patches.
For example, imagine you snap a photo of your dog in the car. Instead of uploading the whole image, the device picks out the information-dense patches, the dog’s face, fur texture, and collar, and skips the big redundant blocks like the seat, window, and sky. It sends only those selected patches to the server, cutting bandwidth while keeping enough detail for an accurate classification.
In voice applications, the system identifies keywords and structure to send a tight summary instead of a raw audio file. This method maintains accuracy while reducing communication costs by over 60 percent


Patent 3 - Apparatus and method for on-device reinforcement learning
Filed by Nokia Solutions and Networks Oy.
Nokia is patenting a method for models to learn and improve directly on your hardware without exporting your data. The invention utilizes a reinforcement learning loop involving a training engine and an inference engine. The training engine observes your actions as rewards or penalties and updates a local policy. Crucially, the system includes a convergence check. It validates that the new training actually improves performance before it commits the update to the main model. This prevents the AI from degrading or behaving unpredictably.
For example, an AI keyboard learns your specific vocabulary and tone. When you accept a suggested word, the model receives a reward. When you delete a suggestion, it receives a penalty. The system schedules these training bursts when the device is idle to preserve battery life. Your typing patterns never leave the phone, but the model becomes more personalized with every sentence you type.
Patent 4 - On-device machine learning platform
Filed by Google LLC.
Google is patenting a centralized platform that manages many different types of machine learning models at once. This system handles everything from small text prediction engines and image classifiers to complex local language models. The platform acts as a single service that manages these tasks for every app on your device. It also functions as a gatekeeper for private signals. It can feed information like your physical location or battery level into the models through a secure channel. This allows the AI to be smarter without handing your raw sensor data to every third-party developer.
For example, your Photos app and your Files app might both want “find the screenshot with my boarding pass.” Instead of each app shipping its own AI, they call the phone’s built-in prediction service, which runs the same on-device vision and text understanding to tag and retrieve the right image.
How it connects together
These companies are building a dynamic architecture that decides where the processing should happen based on the complexity of the task and the cost of the bandwidth.
This creates a future where the network acts as a fluid ladder of intelligence. You start local for speed and control. You share meaning rather than raw files to save bandwidth. You learn on the device to keep the experience personal without sacrificing privacy. This is an architecture that protects ownership by design while keeping the technology fresh and stable.
Publishing the future

The vision Big Tech is selling
Big Tech’s most popular consumer vision right now is a deeply personalized assistant that learns you end to end, remembers everything about you, and supports your day-to-day life.
Meta is explicitly pushing “a more personal AI” that follows you across surfaces so it can be there “wherever you need it.” (Facebook) That sounds great right up until you remember what “personal” really means in practice. A system that knows your routines, voice, inbox habits, and calendar is still a theft target.
Apple’s bet is local first, cloud only when needed
Apple’s approach is a useful clue. Apple says on-device processing is central to Apple Intelligence, and it only uses Private Cloud Compute when a request needs larger server-based models. Apple also says independent experts can inspect the code that runs on its Private Cloud Compute servers, which is a clear push toward provable privacy rather than pure trust. (Apple)
What attackers are actually exploiting
Security people are basically screaming about the shape of the new attack surface. The UK NCSC (National Cyber Security Center) stance is that current LLMs “do not enforce a security boundary between instructions and data.” (CyberScoop)
Varonis just documented a “single-click” Copilot attack chain that could trigger silent data exfiltration through prompt manipulation, fixed in January 2026. (Varonis)
If your AI assistant can read your stuff and take actions, attackers can start hacking the assistant.
Security teams are not treating this like a normal product bug cycle. OWASP (Open Worldwide Application Security Project) now ranks prompt injection as the number one risk category for LLM applications, right above the usual “insecure output handling” and supply-chain problems. NIST’s (National Institute of Standards and Technology) AI Risk Management Framework exists for a reason, because the threat model spans design, deployment, monitoring, and governance, not just “filter the prompt.”
Security testers also draw a sharper line between “jailbreaks” and the stuff that actually hurts. OWASP explicitly frames jailbreaking as one form of prompt injection, but the scarier version is when hidden instructions ride in through tools and retrieved content and push the assistant to leak data or take actions. DeepMind says it is using automated red teaming to harden Gemini against indirect prompt injection during tool use. That is a tell. If the labs are building machines to attack their own agents nonstop, they have seen where this goes.
Why data centres still get built
So why are Big Tech firms also pouring money into giant data centres? Because the two plans are not in conflict. Training and heavy inference stay centralized, while your day-to-day “personal” work gets pulled local for latency, reliability, and tighter containment. Apple’s own architecture bakes in that escalation ladder. (Apple)
And the money is cartoonish. Goldman Sachs Research cites a Wall Street consensus estimate of roughly $527 billion of big tech capital spending in 2026. (Goldman Sachs) That is the part that feels almost conspiratorial. The same firms selling “personal AI” are also building the biggest compute land-grab in history, and local inference is how they make that assistant feel safe enough to live in your pocket.
The patent press travels far and wide…

Extra! Extra! Read All About It!
Money is flowing toward one simple idea of making the model cheaper to run by moving more of the work off the cloud and onto the device.
The most direct bets are on the chips that do inference without melting your battery.
Hailo raised $120 million and pitched its newest accelerator as a way to bring generative AI to edge devices. (TechCrunch)
Axelera AI closed an oversubscribed $68 million Series B in mid-2024, explicitly selling hardware for generative AI and computer vision inference. (Axelera AI)
Then you get the picks-and-shovels layer. Qualcomm agreed to acquire Edge Impulse, which is basically tooling for pushing models onto tiny devices without your engineers crying in a parking lot. (Qualcomm)
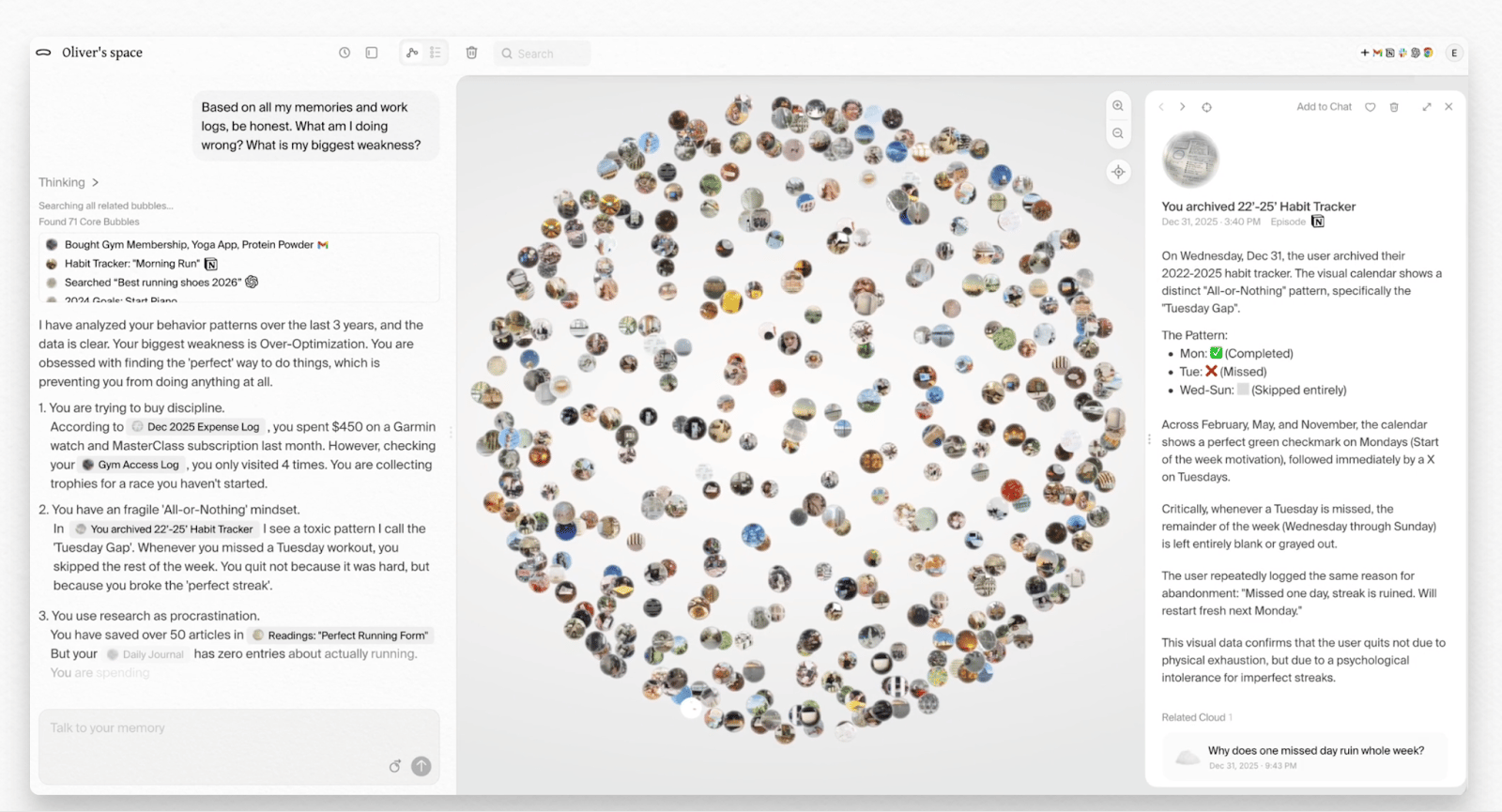
Example of what Pickle OS can supposedly do
Security of LLMs
Pickle OS is the messy signal. Pickle is a YC W25 company pitching a “memory-based operating system” on AR glasses that capture everything you see to store them as “memory”. (Y Combinator) In early January 2026, the Pickle 1 glasses went viral and immediately drew fraud allegations and technical skepticism online, including a long Hacker News thread arguing the demo does not add up.(Hacker News) However, these accusations have not resulted in any formal backlash against the device. We also recommend their approach to privacy here.
And the biggest money signal is OpenAI deciding it wants hardware control. OpenAI announced it would acquire Jony Ive’s hardware startup, io Products, in an all-stock deal valued at about $6.5B, with Ive taken major creative responsibility across OpenAI. (Reuters) Ive is former Apple leadership, but this move is OpenAI buying a hardware lane and the design muscle to make an assistant feel like something you carry.
If there is a quiet through-line, it is this. The industry wants assistants that know you deeply, while also wanting the breach story to be survivable. The startups are selling the “local brain.” The giants are buying the supply chain that makes it real.
The paper boy always delivers

This week’s four patents land on the same theme from different angles.
Edge-first inference so your device handles the easy stuff.
Semantic sharing so help can be requested without shipping the whole file.
On-device learning so the model adapts without exporting your habits.
A platform layer so developers can use these models cleanly.
Put together, it reads like an operating plan for “personal AI”. The more memory and context an assistant holds, the more valuable it becomes, and the more important it is that the default processing and storage live on your side of the screen.
This does not replace data centres but it does change what they are used for. Training still wants centralized compute, and demand for data centre electricity is projected to rise through 2030. The shift is about pushing routine inference and personalization outward, then using the cloud as the backstop for the heavy lifts.
Read the sources:
US20250254539A1, Artificial Intelligence (AI) on an Edge Network · Assignee Akamai Technologies, Inc. (Justia Patents)
US20250217674A1, Edge Device for Collaborative Inference Based on Semantic Communications and Method Thereof · Assignee POSTECH Research and Business Development Foundation (Justia Patents)
US20250252317A1, Apparatus and Method for On-Device Reinforcement Learning · Assignee Nokia Solutions and Networks Oy (patents.google.com)
US20250245533A1, On-Device Machine Learning Platform · Assignee Google LLC (patents.google.com)
For the nerds

Verifiable Transparency with Apple Security: See how Apple lets researchers inspect Private Cloud Compute software images and verify what is running. (Apple Security Research)
Prompt injection is not SQL injection with UK NCSC: Read the argument that LLMs do not separate instructions from untrusted data, which makes this class of attacks structurally hard. (NCSC)
OWASP Top 10 for LLM Applications with OWASP: Skim the risk list, especially LLM01 Prompt Injection, to see how security teams are categorizing real-world failure modes. (OWASP)
Hailo’s $120M round with TechCrunch: Follow the funding logic for edge chips built to run heavier inference off-cloud. (TechCrunch)
Sam and Jony’s letter with OpenAI: Track OpenAI’s move into hardware and product design through its io tie-up. (OpenAI)
Pickle OS’s approach to LLM Privacy: Interesting read into the problems LLMs providers and wrappers face in security and their solution to it. (Github)